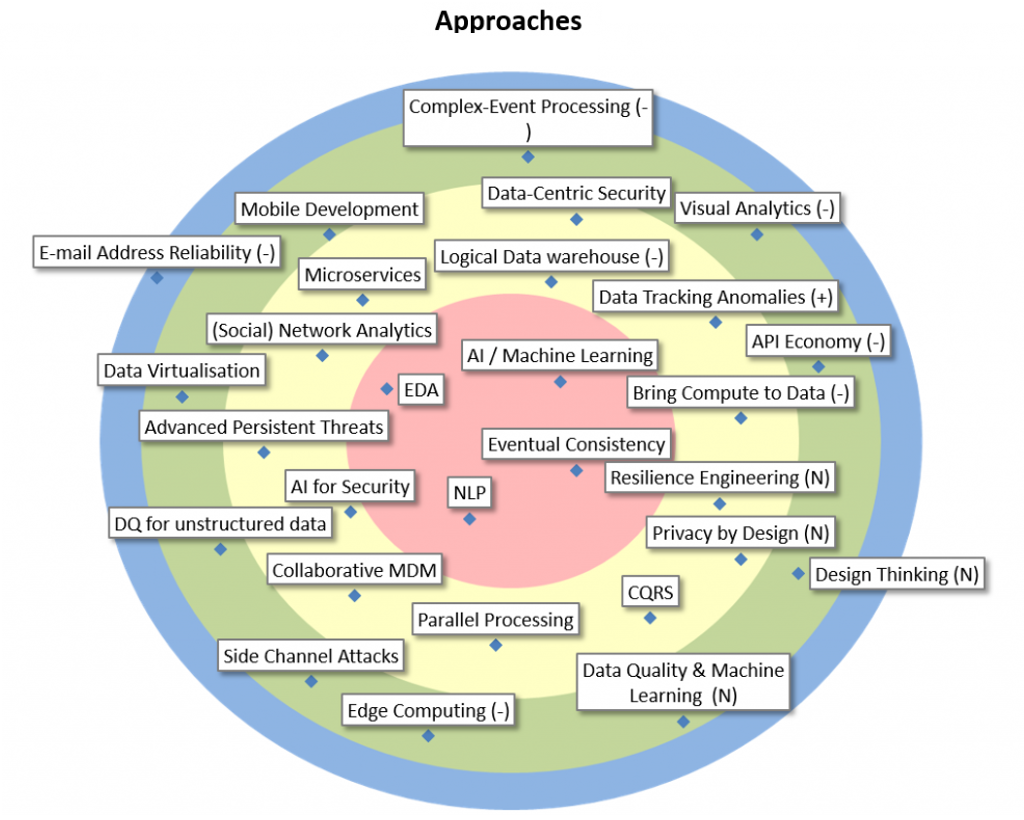
| AI / Machine Learning |
AI is the broader concept of machines acting in a way that we would consider “smart”. Machine Learning is a form of AI based on giving machines access to data and let them learn for themselves. Includes neural networks, deep learning, language processing. A possible application is fraud detection. |
| EDA |
An Event Driven Architecture can offer many advantages over more traditional approaches. Events and Asynchronous communication can make a system much more responsive and efficient. Moreover, the event model often better resembles the actual business data coming in. |
| NLP |
Natural Language Processing as part of AI is a technique to distill information from unstructured textual data, with the aim of using that information inside analytics algorithms. Used for text mining, sentiment analysis, entity recognition, natural language generation (NLG)… |
| Eventual Consistency |
A general way to evolve systems away from too restricitive ACID principles. Using this, and pushing it through on a business level, are the only way to keep systems evolving towards a more distributed, scalable, flexible, and maintainable lifecycle. |
| Bring Compute to Data |
New paradigm, implemented by (Big Data) analytics solutions: offloading front-end analytics or data integration tools in favor of having the calculations executed, as much as possible, by the (database) management systems in control of the data. |
| Data Tracking Anomalies |
Method to detect the causes of data quality problems in data flow between information systems and to improve them structurally. It has an important ROI and facilitates a “win win” approach between institutions. |
| Data-Centric Security |
Approach to protect sensitive data uniquely and centrally, regardless of format or location (using e.g. data anonymization or tokenization technologies in conjunction with centralized policies and governance). |
| Logical Data warehouse |
A data warehouse architecture that makes all types of data available for analytical tools in a transparent way. It hides, manages, and encapsulates the complexity and particularities of the underlying data source management systems, while Bringing Compute to the Data. |
| Microservices |
Independently maintainable and deployable services, which are kept very small (hence, ‘micro-‘), make an application, or even large groups of related systems, much more flexibly scalable, and provide functional agility, which allows a system to rapidly support new business opportunities. |
| (Social) Network Analytics |
Social network analytics (SNA) is the process of investigating social structures (i.e., relations between people and other entities such as companies, addresses, …) by the use of network and graph theory, as well as concepts from sociology. |
| Advanced Persistent Threats |
New type of threats used to perpetrate a long-term computer attack on a well-defined target. Closely resembles industrial espionage techniques. |
| AI for Security |
Non-traditional methods improving analysis methods in the security technology of systems and applications (e.g. user behaviour analytics). |
| Collaborative MDM |
Collaborative and organized management of anomalies stemming from authentic sources, by their official users. |
| Parallel Processing |
Spreading data and calculations over the available memory and computing power of several machines (nodes), such that queries, calculations, tranformations, etc. are delivered faster. Hadoop Ecosystems and MPP (Massively Parallel Processing) databases implement this. |
| CQRS |
Command and Query Responsability Segregation: keep the parts of a system that handle querying and the parts that handle state changes separate. This allows for more flexible and scalable distributed architectures. |
| Privacy by Design |
Privacy by design calls for privacy to be taken into account throughout the whole engineering process. The European GDPR regulation incorporates privacy by design. An example of an existing methodology is LINDDUN. |
| Resilience Engineering |
Robustness is the ability of a system to cope with errors during execution and with erroneous input. Example techniques are fuzz testing, mutation testing, fault injection or chaos engineering. Is often part of DevOps. |
| API Economy |
API’s, to connect services within and across multiple systems, or even to 3rd parties, are becoming prevalent and push a new business model, centered around the integration of readily available data and services. They also help with loose coupling between components. |
| Visual Analytics |
Methodology and enabling tools allowing to combine data visualization and analytics. Allows rapidly exploring, analyzing, and forecasting data. This helps modeling in advanced analytics, and to make modern, interactive, self-service BI applications. |
| Complex-Event Processing |
A combination of Event Driven Architecture and Analytics solutions that allows for real-time responses to certain patterns of events coming into the system. Typically, CEP will use a stream of low-level events to generate some higher-level, more interesting events. |
| Mobile Development |
Set of techniques, tools and platforms to develop web based and platform-specific mobile applications. |
| Data Virtualisation |
Methods and tools to access databases with heterogeneous models and to facilitate access for users using a virtual logical view. |
| DQ for unstructured data |
Tools and management strategies that allow for sharing increasingly large unstructured data. Those tools use Text Mining, NLP, social data, … |
| Side Channel Attacks |
Type of attacks exploiting the physical weaknesses in the implementation of a system (e.g. power consumption, timing, hardware faults, EM waves, etc. ). |
| Edge Computing |
Information processing and content collection and delivery are placed closer to the endpoints to fix high WAN costs and unacceptable latency of the cloud. |
| Data Quality & Machine Learning |
How to apply Machine Learning and IA to improve Data Quality Tools efficiency, specifically, for the “data matching” step. |
| Design Thinking |
Approach used to improve the design from software to products and services. Empathy for users and the gathering of insight into their needs and motivations is crucial. Used for digital innovation with focus on people. User-centric design is an important element of this approach. |
| E-mail Address Reliability |
Email address reliability in databases : concepts, tools and methods (including the use of Data Quality Tools) to improve and maintain email address quality. |