Business Goals, Problems, Opportunities…
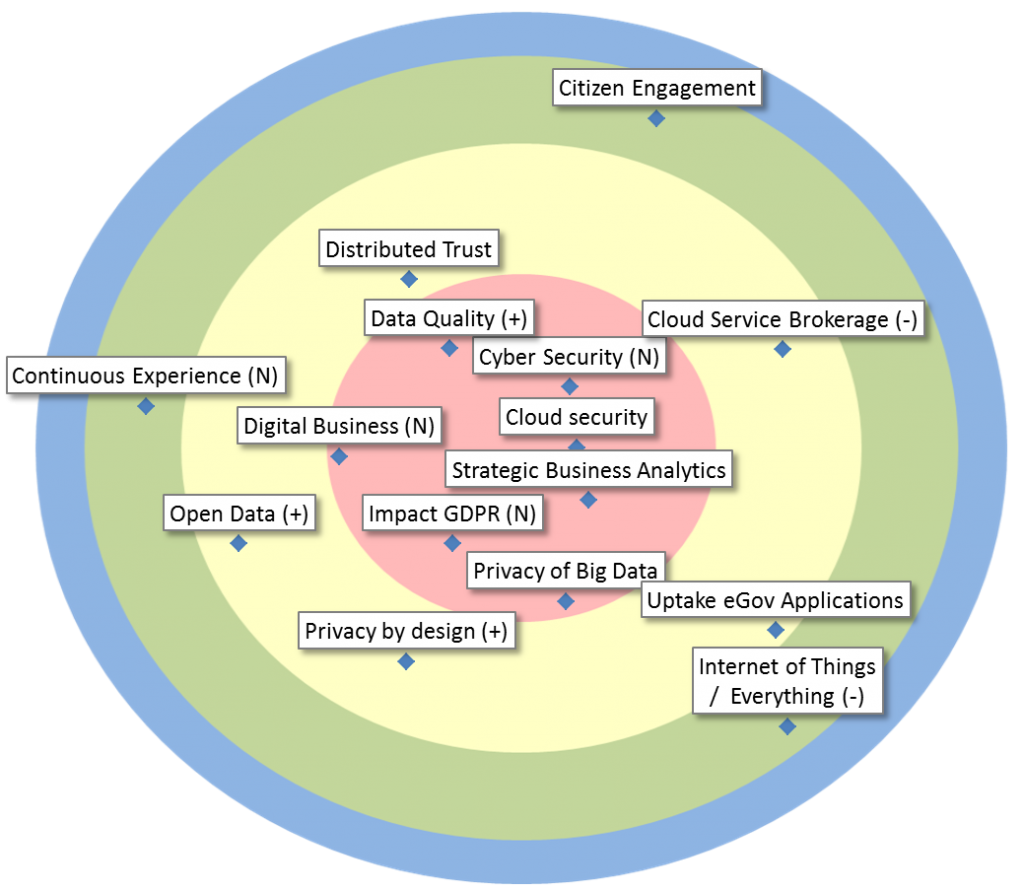
| Cloud security | Sub-domain of Cloud Computing, encompassing all aspects related to the security of and cryptography in the cloud, whether private, public or hybrid. |
| Cyber Security | Technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access (e.g. in the context of cyber warfare). |
| Data Quality | Tools, methods and architectures to improve data quality and to manage information, taking into account cost-benefit ratio. (Includes Master Data Management) |
| Digital Business | “The creation of new business designs by blurring the boundaries between the digital and physical worlds due to the convergence of people, business and things” (Gartner). New technologies like IoT, analytics, machine learning, … are used to realize the digital transformation. |
| Impact GDPR | The GDPR has been approved and we have less than two years to become compliant. What measures should be taken at Smals and within the sector? |
| Privacy of Big Data | Truly anonymizing personal identifiable information (PII) is hard. Therefore, analytics on PII or data derivation from PII should be done with utmost care. What measures can we take and what technologies exist to protect PII, while still allowing analytics? |
| Strategic Business Analytics | Driven by corporate strategy, make use of state-of-the-art Analytics (techniques and platforms) to drive processes and support (informed, measured, evaluated) policy-making in strategic domains. Transcends what is possible with classical Statistics or BI. |
| Cloud Service Brokerage | Providing support with added value, such as security and integration, to help customers of Smals use cloud services efficiently and correctly. |
| Distributed Trust | Use of intermediary parties as trusted authority is widespread in government contexts. How to reduce trust in such authorities or eliminate them altogether? This can result in more efficient administration. Blockchain technology often helps, but usually, more is needed. |
| Open Data | Data interoperability based on documented “open data” for citizens, enterprises, … (and in some cases based on web semantics norms) |
| Privacy by design | Privacy by Design is an approach to systems engineering which takes privacy into account throughout the whole engineering process. |
| Uptake eGov Applications | Methods and techniques for a better use (uptake) of eGov applications by citizens and other users. User-centric design is an important element of this approach. |
| Citizen Engagement | The use of IT to stimulate voluntary participation and self-organization of citizens to create societal added value. |
| Continuous Experience | Users can interact with an application in a multistep sequence that may last through an extended period of time. The experience seamlessly flows across multiple devices and interaction channels, including non-digital and analog ones, that fulfill the customer journey. |
| Internet of Things / Everything | With the Internet of Things (IoT), many (electromechanical) objects, along with a vast amount of sensors and actuators, become connected to the internet and generate an abundance of data, allowing all kinds of new business. |
